There are two very cool things. They recognize Security-Tags, and have a good process that will help us.
Security-Tags:
The first one is that they refer to “Data-Tagging”, which is general IT discussion toward a solution. This is very similar to the “Healthcare Privacy & Security Classification System” that we have defined and created profiles for – One example is the DS4P. This concept of Security-Tags has been integrated into XDS (XCA, XDM, XDR), and also into HL7 FHIR. This is a useful vector for the purpose of enforcing Access Controls including Privacy aspects.This is, as Creative Commons indicates, not sufficient.
Consent Language Communications:
The more cool thing is the concept of applying the methodology that Creative Commons have done for Copyright/License to Privacy Consent. They have created a reasonable set of Licenses that can be used in a very useful and actionable way. For example, my blog is published under the
"Attribution-NonCommercial-ShareAlike 3.0 Unported" License. Which is understandable by many means of reading and processing.
With Patient Consent, we struggle with a similar problem to the Copyright/License problem that Creative Commons initially addressed. The language that organizations want to use is written once, by them, for their purposes; thus the language at each organization must be read and understood. Most of the time the language is in legal terms and thus not very consumable by non-lawyers, and also not consumable by computers. The result of this confusion is that the humans involved are not well informed. Also true is the failure in the computers that should be protecting the data, which includes providing access to those that are authorized.
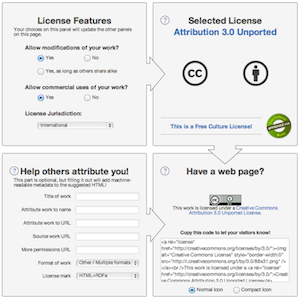
Creative Commons have come up with a very useful “Design and Rational” that creates three layers that are very useful with Patient Consent.. There is the “Legal Code” that includes the legal specifics. There is the Human Readable, which is specialized for normal humans to read, possibly translated into multiple languages and such. There is a Machine Readable form, that is structured and coded.
I will note that the current Machine Readable form is very much like what we did with IHE-BPPC; that is it is most of the time simply an established URL per policy. Thus all that is necessary for the computer to know which license is applicable is to see which of the Creative Commons URLs are applied. The main difference is that they host and thus create the machine readable URLs. Whereas with IHE-BPPC the creation and publication is a ‘local matter’. Creative Commons "REL" is a similar container as the CDA structure defined by IHE-BPPC, or the potential future HL7 FHIR ConsentDirective could be..
As applied to Healthcare Privacy Consent:
So, the result of Creative Commons effort might be a set of boilerplate Privacy Consent policies. The equivalent of what I have referred to as Opt-IN, Opt-OUT, OPT-OUT-breakGlass, etc.Using the Creative Commons methodology this would result in a set for each of these: Legal Code, Human Readable, and computable URL.
This is not an easy thing to write. I have been involved in many workgroups that have worked on these. In each case a number of people, mostly lawyers, wanted to have special wording in for their special cases. I presume that Creative Commons has mechanisms to work through these differences.
We might even get some cool icons like they have for the License, where the icons visually represent the essence of the language.
Patient Friendly Interview Process:
Going one step further, Creative Commons have created an interview process for people that want to apply a Creative Commons License to their works.The interview process walks the person through a set of decision points. This results in a recommended CC Mark.
This today is not all that 'friendly' and the population that are Patients (healthcare consumers) likely need far more 'friendly' interfaces. However the concept is similar in that one tends to narrow the choices over time.
There are a few pilots that have attempted this, including one from HHS/ONC that resulted in some very interesting observations.
Conclusion:
I have said all the above before, in 2009, Consumer Preferences and the Consumer. The difference is that Creative Commons might bring their methodology and thus some maturity to the conversation.Blog resources: Patient Privacy controls (aka Consent, Authorization, Data Segmentation)
- Enabling Patients to Delegate Healthcare Information Access Authority
- Define Atom -- Too many definitions in use today
- Defining Privacy
- Safety vs Privacy
- Privacy Consent State of Mind
- Defining Privacy
- Universal Health ID -- Enable Privacy
- Texas HIE Consent Management System Design
- Simple and Effective HIE Consent
- IHE - Privacy and Security Profiles - Basic Patient Privacy Consents
- Data Segmentation - now I know where the term comes from